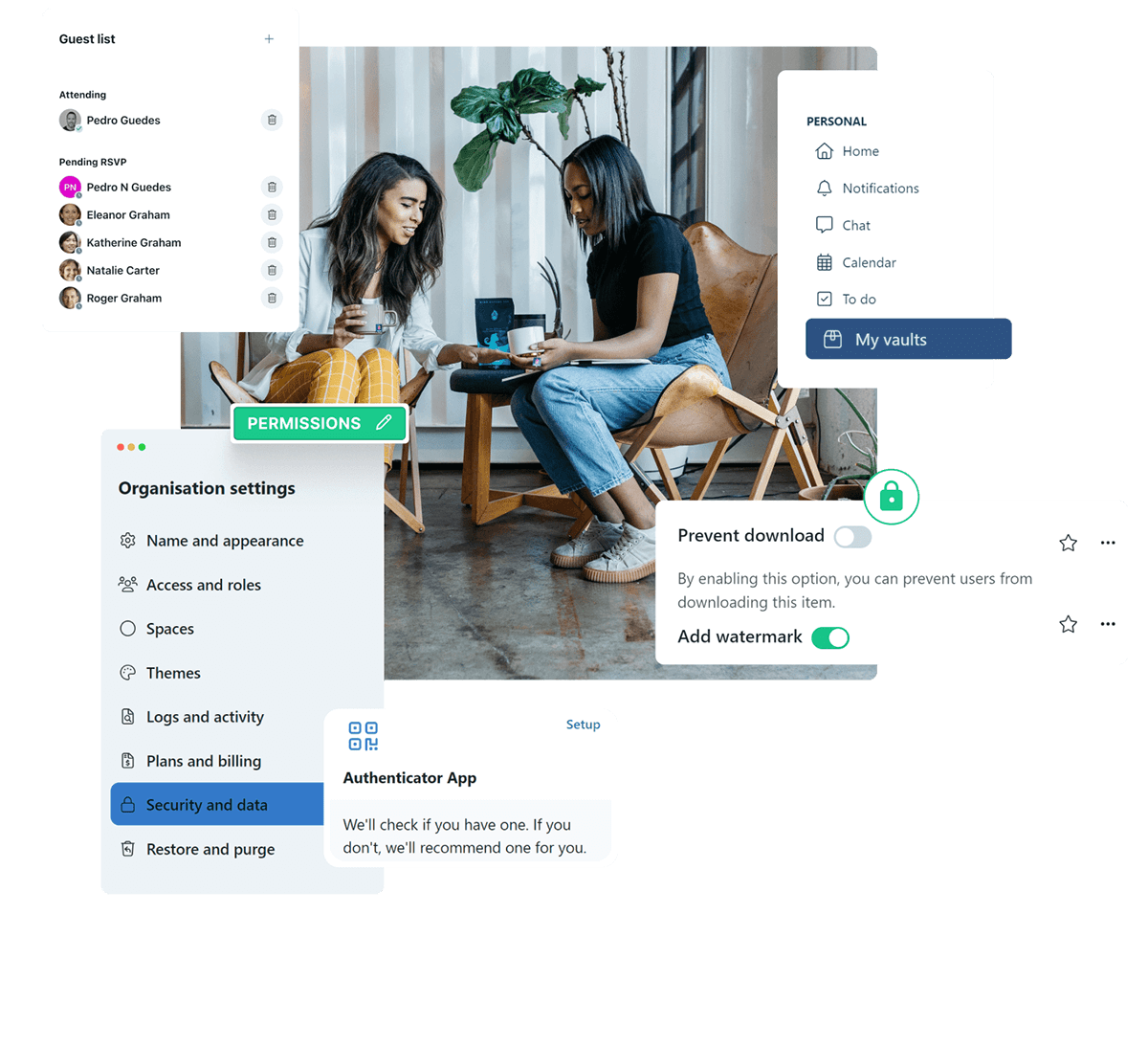
Keeping your family data secure across generations
The safety of your family and business information is our top priority, so we employ gold-standard practices that keep your data secure and private.
Built on a Foundation
of Compliance
We maintain the highest of standards through
our infrastructure providers

Digital Ocean Hosting
Hosted on DigitalOcean, providing top notch security protections including AICPA SOC 2 Type II and SOC 3 Type II infrastructure and Cloud Security Alliance (CSA) STAR Level I certification.
AWS Storage
All file storage uses Amazon Web Services which are SOC 1, 2, and 3 compliant infrastructure.
Cloudflare
As an additional security measure, we employ the SOC 2 Type II-certified Content Delivery and Web Application Firewall infrastructure of Cloudflare, an ISO 27001 certified organisation.